Wireguard is a new, fast efficient VPN that’s likely to be merged into the linux kernel. If you haven’t heard about it yet, then head over here for a quick overview. Wireguard only works on UDP though and in this post, we’ll see how to use it by tunneling UDP over TCP
Now on Linux, udptunnel, socat and even tunneling UDP over SSH are all great options but I’m stuck with a Windows
machine so need something that’ll work cross platform - and that’s where I came across Secure Socket Funnel
For a Wireguard windows client - download one from Tunsafe
Assuming Wireguard is listening on 2194 with config like this
[Interface]
Address = 10.200.200.1/24
SaveConfig = false
ListenPort = 2194
FwMark = 0xca6c-
On the server, generate a keypair for the client:
wg genkey > secret.key wg pubkey < secret.key > public.key -
On the server, Add peer configuration to your
/etc/wireguard/wg0.conffile[Peer] PublicKey = <paste in the key from public.key> AllowedIPs = 10.200.200.4/32 -
Restart wireguard with
sudo systemctl restart wg-quick@wg0 -
Start SSF on the server to listen on 443 like so
ssfd -p 443 -
On the client, add a configuration file like
C:\Program Files\TunSafe\Config\myserver-tunnel.conf[Interface] Address = 10.200.200.4/24 # this should match what you added to the peer section on the server PrivateKey = <private.key contents> [Peer] PublicKey = <This is the server's public key> Endpoint = localhost:2194 # Yep - localhost. Our tunnel will take care of shipping this over to the server AllowedIPs = 0.0.0.0/0 PersistentKeepalive = 21 -
Now run the ssf client like so:
ssf -p 4443 -U 2194:<server>:2194 <server> -
After this, you should be able to connect to the VPN using the tunnel
Is it any good?
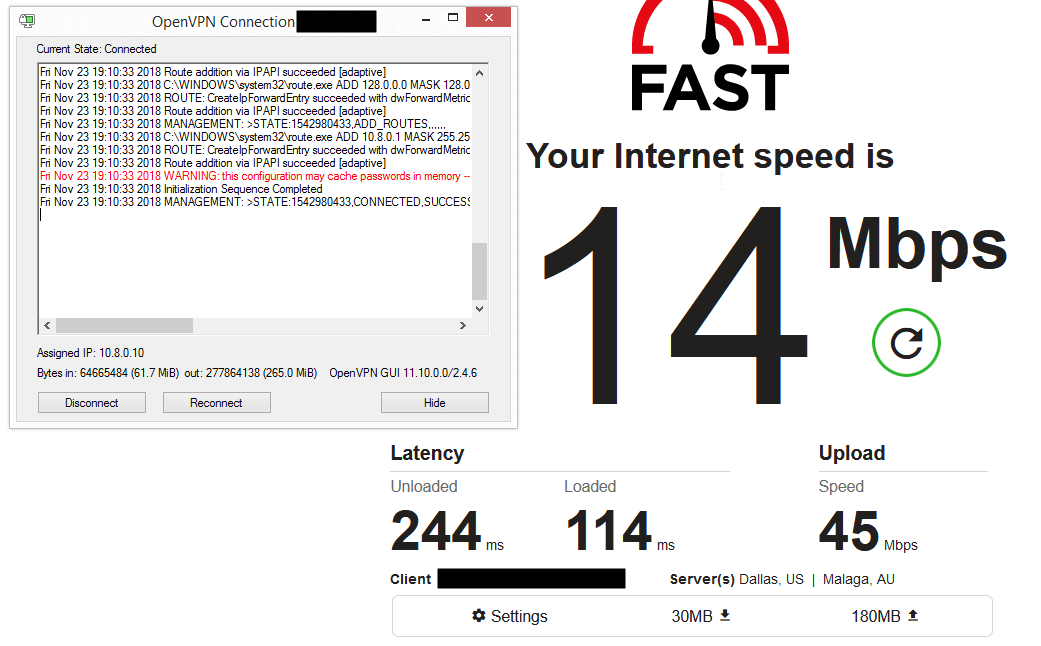
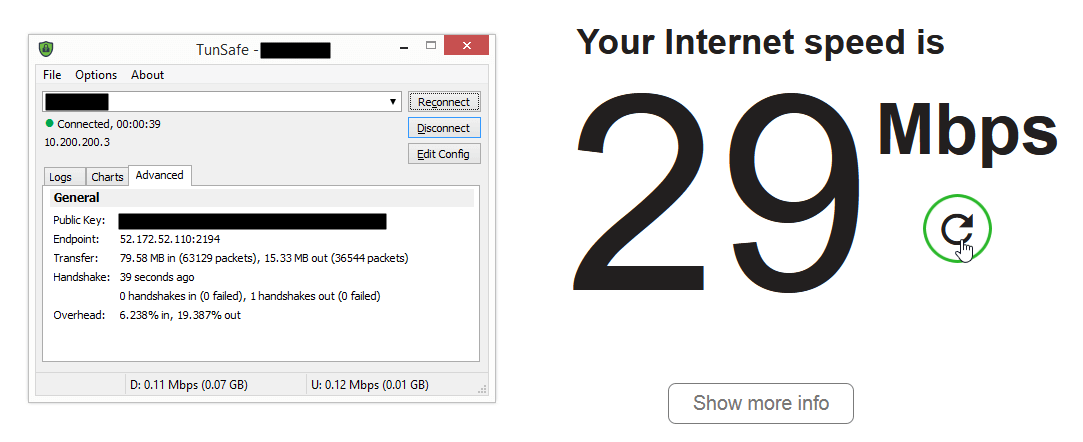
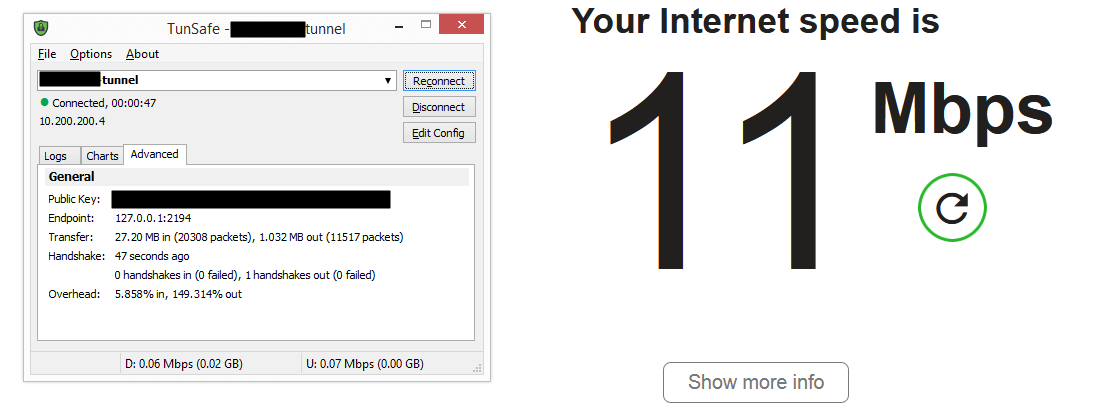
So in my totally unscientific tests, it performs about as well as Openvpn. I tested bandwidth using fast.com while on a wifi connection at home.
| OpenVPN | Wireguard | Wireguard UDP over TCP |
|---|---|---|
|
|
|
And that’s good enough for me as it lets me use a single server for either a TCP or a UDP connections based on what’s available.
Making things permanent
Running ssfd as a service
-
On the server, create
/etc/systemd/systemd/ssfd.service[Unit] Description=SSF Daemon After=network.target [Service] # fixup paths below based on where you have downloaded ssf WorkingDirectory=/home/raghu/ssf ExecStart=/home/raghu/ssf/ssfd -p 443 Restart=on-failure [Install] WantedBy=multi-user.target -
Enable the service to run on boot
sudo systemctl daemon-reload sudo systemctl enable ssfd sudo systemctl start ssfd # now if you check status of the service sudo systemctl status ssfd # you should see sth like: ssf sudo systemctl status ssfd ● ssfd.service - SSF Daemon Loaded: loaded (/etc/systemd/system/ssfd.service; enabled; vendor preset: enabled) Active: active (running) since Sun 2018-11-25 14:44:46 UTC; 7min ago Main PID: 88092 (ssfd) CGroup: /system.slice/ssfd.service └─88092 /home/raghu/ssf/ssfd -p 443 Nov 25 14:44:46 openvpnserverVM ssfd[88092]: [tls] key password: <>